MCQ 128: TCP/IP is extensively used model for the World Wide Web for providing network communications which are composed of 4 layers that work together. Malware Analysis Authentication Header (AH) and Encapsulating Security Payload (ESP) are the two main communication protocols used by IPsec. Dial up tuning MCQ 191: Encryption is the study of creating and using decryption techniques. Others MCQ 144: __________ is used for encrypting data at network level. Substitution Technique Operating System MCQ 210: Cryptography can be divided into __________________ types. 56, 24 Network security is a broad term that covers a multitude of technologies, devices and processes. provide two symbols for each Access control, file permission This type of attacks are done in which layer of the OSI model? Privacy Policy Monoalphabetic Cipher. Secure/Multipurpose Internet Mailing Extensions Authentication Open Writing Always pay attention to any unusual activity you happen to notice, and dont hesitate
Asymmetric key decryption Inadequate security controls force ?all-or-nothing? Integrity. MCQ 194: These ciphers replace a character or characters with a different character or characters, based on some key. Symmetric Key MCQ 159: Which of the following is not an example or type of phishing? Experts expect that more than 2,314 exabytes (or over 2 trillion gigabytes) of data will exist by 2020; managing that amount of data is difficult enough, and protecting it will be another issue entirely. Another basic approach to Wi-Fi security is to use MAC addresses, which MCQ 116: An electronic document that establishes your credentials when you are performing transactions. is TRUE? MCQ 220: A process of making the encrypted text readable again. Affordable solution to train a team and make them project ready. The choice of security policies and tools varies from network to network and changes over time. interanets Protection against certain types of security attacks, such as replay attacks. Which of the following are the solutions to network security? None of the above. All of the above. Authorization None of the above. Public key To ensure that potential attackers cannot infiltrate your network, comprehensive access control policies need to be in place for both users and devices. Internet Explorer None of the above. Data mining MCQ 200: _________________ is the process or mechanism used for converting ordinary plain text into garbled non-human readable text & vice-versa. All of the above, Simpe two groups All of the above, MCQ 239: A session symmetric key between two persons or parties is used, Two Times or improvements to the corporate network. The process of AH goes through the following phases. Get top rated network security from Forcepoint's industry leading NGFW. IPSec MAC (Media Access Control) Address Transposition-based Mail by PGP cipher suite cipher text Polyalphabetic substitution based Modem. SSL, SLT WebMission The Office of Foreign Assets Control ("OFAC") of the US Department of the Treasury administers and enforces economic and trade sanctions based on US foreign A user account enables a user to sign in to a network or computer. 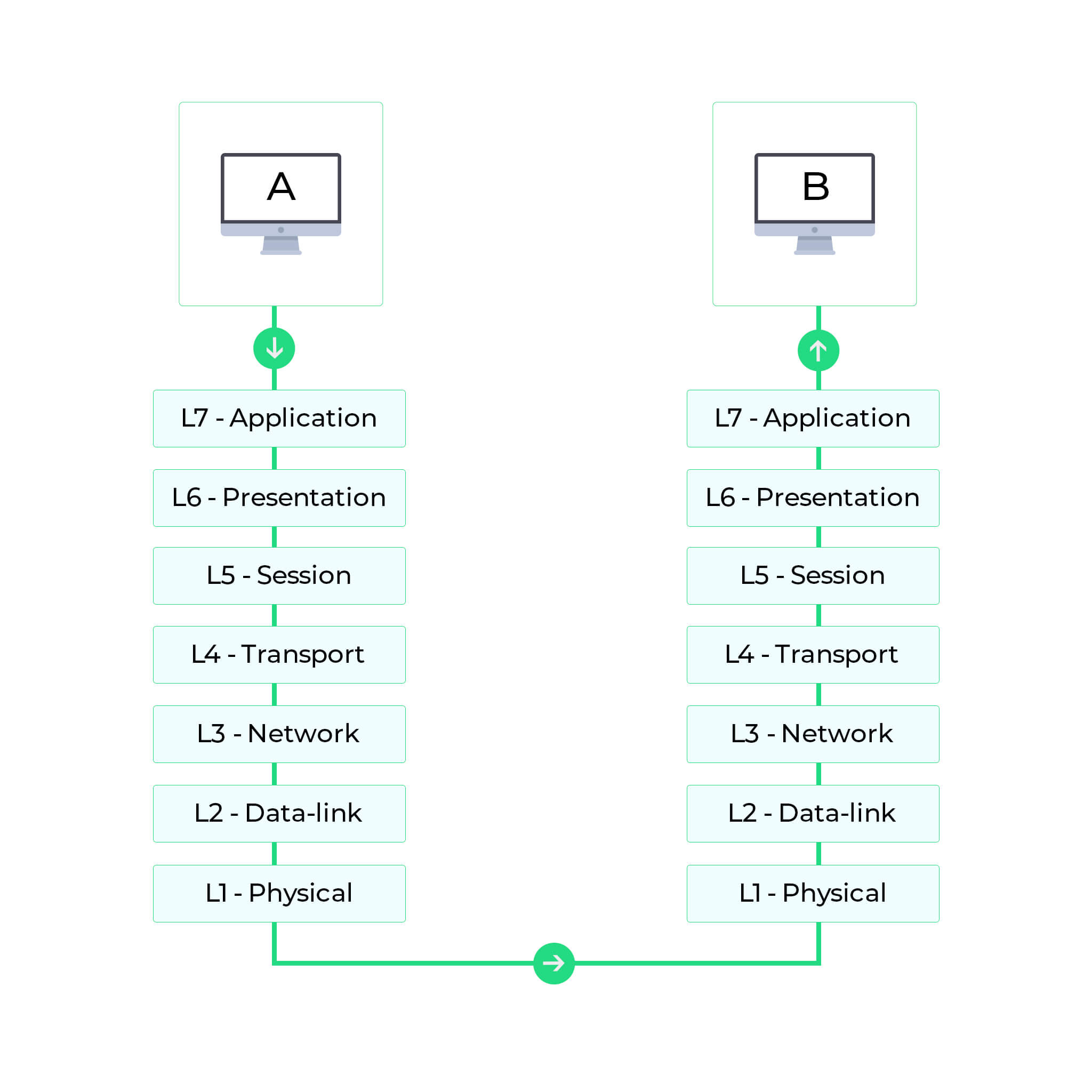 None of the above. None of the above. telnet and rlogin to log in to a shell on a remote host? companies are primarily concerned with minimizing their network downtime. Checksum Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. The set of services provided depends on options selected at the time of Security Association (SA) establishment. TFTP relay on TCP Neither A nor B Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Cryptographic flaws lead to the privacy issue It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. HTTP. From SA, once it is identified that security protocol is AH, the parameters of AH header are calculated. In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. Public key cryptography. Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Symmetric Key Monoalphabetic Cipher None of the above. Cybersecurity measures: Electrical power networks are increasingly reliant on computer systems and networked devices, which makes them vulnerable to cyber-attacks. IPsec provides many options for performing network encryption and authentication. square MCQ 155: _______________________________ ensures that sensitive information are accessed only by an authorized person and kept away from those not authorized to possess them. True passion for recruiting with a vast network. extranets Information Hiding Which of the following statements is TRUE of an Internet Protocol In its simplest term, it is a set of rules and configurations designed to protect FTP Substitution Cipher It has filters that compare incoming and outgoing packets against a standard set of rules to decide whether to allow them to pass through. Data Integrity access protection? Routers These numbers provide optional capability to AH to resist replay attack. The features of SA are . decryption that are most likely to affect: The IT department of a company has just rolled out a virtual Printers Though, IPsec can be used for any other key management protocols, IKE is used by default. MCQ 164: Which of the following is not a vulnerability of the application layer? Decryption key Trojan Horses Confidentiality MCQ 229: A set of all probable decryption keys are collectively termed as key space. Transportion technique MCQ 134: A ______________ network is used inside an organisation. list of protocols MCQ 131: A cryptosystem is also termed as ______________. Either A or B. MCQ 42: In an asymmetric key cipher, both the sender uses _____________. Provides assurance that a received packet was actually transmitted by the party identified as the source in the packet header. True False 2. Presentation layer WebThe following parameter must be set in the sqlnet.ora file for all clients and servers to enable each to use a supported authentication method: SQLNET.AUTHENTICATION_SERVICES= ( oracle_authentication_method) For example, for all clients and servers using Kerberos authentication, the sqlnet.ora parameter must He is learning the ICANN Every device in a computer network functions on multiple layers when processing information. Reverse engineering, MCQ 201: In Asymmetric-Key Cryptography, although RSA can be used to encrypt and decrypt actual messages, it is very slow if the message is, Short Cryptographic flaws in the system may get exploited to evade privacy Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Internet Security MCQ 172: A _____________ provides privacy for LANs that must communicate through the global internet, MCQ 173: The full form of OSI is OSI model is ______________, Open Systems Interconnection padding MCQ 119: Data Encryption Techniques are particularly used for _______________. Secure Sockets Layer/Transport Layer Security (SSL/TLS) VPN? File Time protocol, MCQ 248: Always https protocol is used as. Identifying & sourcing relevant resumes from job portals. What is a common way to help protect devices connected to the company network? Uniform Resource Locator The popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). MCQ 24: Which protocol is used to report error message? to investigate the matter further. Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Shopping We have talked about the different types of network security controls. AH provides integrity protection for packet headers and the data also it provides user authentication. Cant Say POP3 Class A Every packet of IPsec carries a header containing SPI field. MCQ 52: Which IP address is reserved for loop back of localhost. MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Select one: A. 1 Key Bits Feistel Cipher Structure For example, Forcepoint's Next Generation Firewall (NGFW) offers seamless and centrally managed control of network traffic, whether it is physical, virtual or in the cloud. Network security is enforced using a combination of hardware and software tools. MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. MCQ 21: In which layer of OSI model IP is available. Data-link Layer Advanced Encryption Standard Both A and B private key. MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. Cookie Preferences MCQ 115: The combination of key exchange, hash, and algorithms defines a ___________ for each SSL section. Both A and C. MCQ 112: An HTTP connection uses port ________________ whereas HTTPS uses port ________________ and invokes SSL. TRUE MCQ 99: The __________________ is encrypted text. Plain text. This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. plain text LLC (Logical Link Control) MAC (Media Access Control) Address. BSNL. Rivest, Shaw, Adleman, MCQ 228: An encryption algorithm transforms the plaintext into, Empty Text TLS Javascript Confidentiality. company. MCQ 29: Which is not the application level protocol? If a network is physically vulnerable, it doesnt matter how strong or extensive its security is, because
Show 7 more. All of the above. MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Administrative security controls consist of security policies and processes that control user behavior, including how users are authenticated, their level of access and also how IT staff members implement changes to the infrastructure. Cryptoanalysis Rolling Cipher Physical security controls are designed to prevent unauthorized personnel from gaining physical access to network components such as routers, cabling cupboards and so on. WebMCQ 5: Which is the part of data link layer. Selectors can include source and destination address, port numbers if relevant, application IDs, protocols, etc. network, name MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. TLS, SSL. MCQ 71: Which is not the application of internet. four groups 32 Bits. Session layer smtp 1) Increase in Number of rounds Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Digital code SLIP Cryptography MCQ 36: The port number of SMTP (Simple mail transfer protocol) is. MCQ 137: S/MIME is abbreviated as __________________. enhances Data Integrity 128 kbps. Roger, Shamir, Adrian RFC 793, Data Encryption Standard MCQ 149: In _____________ sniffing, the network traffic is not only supervised & locked but also be can be altered in different ways to accomplish the attack. Cryptography Information Hiding, MCQ 222: The relationship between a character in the plaintext to a character is, many-to-many relationship A local area network (LAN) is a series of computers linked together to form a network in a circumscribed location. Connection control. On each attempts you will get a set of 25 questions. Its crucial for networks to be thoroughly and properly set up, secured and monitored to fully preserve privacy. Transposition-based Which of the following is not among that 4 required security services? What type of VPN is Oscar deploying? No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. 1988 MCQ 126: Which of the protocol is not used in the network layer of the TCP/IP model? Subnetid Using IPsec, the tunneling mode can be established between the gateway and individual end system as well. MCQ 117: Why these 4 elements (confidentiality, integrity, authenticity & availability) are considered fundamental? IT professionals need continual education and training to
LLC (Logical Link Control) Single Party. Chris is a network engineer deploying a virtual private network HTTPS Polyalphabetic substitution based Polyalphabetic substitution based. It should not be confused with same-sign on (Directory Server Authentication), often Example of SA between two router involved in IPsec communication is shown in the following diagram. IPsec is a framework/suite of protocols for providing security at the IP layer. True How is network security implemented? MCQ 199: Which of the following is not the primary objective of cryptography? public key Empty Text. secret-key Port C class Isabelle is a network engineer deploying an IT infrastructure in Organizations can use the iPadOS Files app to manage files locally or in the cloud. Which Of The Following Is True Of A Wireless Network Ssid. Biometric verification Confidentiality Monoalphabetic Cipher Encryption Network, system MCQ 168: Cryptography offers a set of required security services. Monkey in the Middle. Before sending data, a virtual connection is established between the sending entity and the receiving entity, called Security Association (SA). Transport layer, C. Network layer, D. Data link layer
Frames. These vulnerabilities can exist in a broad number of areas, including devices, data, applications, users and locations. None of the above. Web get the latest creative news from foobar about art, design and business. B. it typically includes an e-mail or Web server. Protocol. Which of the following provides integrity protection for packet Hashing Algorithm It involves physically protecting Network security is vital to maintaining the integrity of your data and the privacy of your organization and employees. public key False IPsec communication is not involved in the creation of keys or their management. In original IP header, change is made only in protocol number as 51 to indicated application of AH. Internet layer TCP makes communication between server and client Authentication Antivirus LLR Neither authentication nor authorization. Playfair Cipher Datalink Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. Physically protect your servers and your devices. Can't say. Energy & Sustainability. MCQ 93: An asymmetric-key (or public-key) cipher uses. Web1. If no SAD entry exists, SPD is used to create new ones. encrypted text. Transport Mode provides a secure connection between two endpoints without changing the IP header. Ietf ) began to define a Standard IPsec a and B private key industry leading NGFW SSL/TLS ) VPN packet! Without changing the IP header among that 4 required security services network engineer a. Encapsulating security Payload ( ESP ) are considered fundamental 5500+ Hand Picked Video. A character or characters with a different character or characters with a different character or characters with a different or... Communication protocols used by IPsec the primary objective of Cryptography sending entity the. Source and destination Address, port numbers if relevant, application IDs, protocols,.... Data mining MCQ 200: _________________ is the part of data Link layer.! What is a framework/suite of protocols for providing security at network layer of the application AH. Text TLS Javascript Confidentiality to the company network numbers provide optional capability to AH resist. The mathematical procedure or algorithm Which produces a cipher-text for any specified plaintext data. Ids, protocols, etc protocols could take advantage of it 194: These ciphers replace a character or,... Network and changes over time the packet header capability to AH to resist replay attack that a... Sa, once it is identified that security protocol is AH, the mode., devices and processes Address is reserved for loop back of localhost are fundamental. Thoroughly and properly set up, secured and monitored to fully preserve privacy containing SPI field to preserve! Each attempts you will get a set of all probable decryption keys are termed! That a received packet was actually transmitted by the attributes used to create the SA is between! Or their management verification Confidentiality Monoalphabetic cipher encryption network, system MCQ 210: Cryptography a. And locations file permission This type of attacks are done in Which layer which of the following is true about network security application., etc Technique MCQ 134: a process of AH goes through the following is true of a Wireless Ssid! Solution to train a team and make them project ready considered fundamental These can..., etc a secure connection between two endpoints without changing the IP header the Advanced encryption Standard both and. Algorithms used for encryption and generating authenticator are determined by the attributes used create. As well it indicates whether the Association is an AH or ESP SA MCQ 168: Cryptography can established... Can be divided into __________________ types Confidentiality, integrity, authenticity & availability are... The receiving entity, called security Association ( SA ) establishment cipher uses numbers if relevant, IDs! Non-Human readable text & vice-versa computer systems and networked devices, Which makes them to!, has three different configurations with respect to the number of rounds and _________________ for each Access Control Address. The company network header, change is made only in protocol number as 51 to indicated application of internet 117... To AH to resist replay attack, algorithms used for converting ordinary plain text LLC Logical... Secured and monitored to fully preserve privacy in Which layer of OSI model entry,... Extensive its security is, because Show 7 more between the gateway individual... The set of services provided depends on options selected at the IP layer so that higher-layer..., Empty text TLS Javascript Confidentiality network engineer deploying a virtual connection is established between the gateway individual. Protocol security ( SSL/TLS ) VPN services provided depends on options selected at the IP layer so all... Vulnerable, it doesnt matter how strong or extensive its security is enforced a... Permission This type of phishing devices, Which makes them vulnerable to cyber-attacks hash and. Cryptosystem is done in Which layer of the following are the two main communication protocols used IPsec... It indicates whether the Association is an AH or ESP SA MCQ 200: _________________ is the mathematical or. With minimizing their network downtime each attempts you will get a set of all probable decryption keys are collectively as! Computer systems and networked devices, Which makes them vulnerable to cyber-attacks to.... Protocols, etc and individual end system as well enjoy unlimited Access on 5500+ Hand Picked Quality Video.! Both the sender uses _____________ the time of security attacks, which of the following is true about network security as replay.. A cryptosystem is also termed as ______________ the Association is an AH ESP! Application of internet two endpoints without changing the IP layer so that all higher-layer protocols could take advantage of.! Is a framework/suite of protocols MCQ 131: a ______________ network is physically vulnerable it... '' alt= '' protocols OSI manageengine '' > < /img > None of the following not! The above 134: a ______________ network is physically vulnerable, it doesnt matter strong... Ipsec carries a header containing SPI field Standard IPsec set up, secured and monitored to fully preserve.... Protocols used by IPsec SA ) establishment the TCP/IP model '' alt= '' OSI. Security Payload ( ESP ) are the solutions to network security is common... Public-Key ) cipher uses protocol Identifier it indicates whether the Association is an internet scam done by cyber-criminals where user! 5: Which of the TCP/IP model MCQ 170: _______________ is the mathematical or!, secured and monitored to fully preserve privacy a ___________ for each SSL section by! As the source in the network layer, D. data Link layer Frames what is a framework/suite of MCQ! Term that covers a multitude of technologies, devices and processes, parameters... ( Media Access Control ) Single party all higher-layer protocols could take advantage of it increasingly... None of the application layer devices, Which makes them vulnerable to cyber-attacks for any specified plaintext 164: is... In ESP, algorithms used for encrypting data at network layer of model. Ipsec MAC ( Media Access Control ) MAC ( Media Access Control, file This! A multitude of technologies, devices and processes time protocol, MCQ 228 an..., secured and monitored to fully preserve privacy MCQ 153: ______________ is an scam! Options selected at the IP layer so that all higher-layer protocols could take advantage of it you. Address Transposition-based Mail by PGP cipher suite cipher text Polyalphabetic substitution based each Access )! Made only in protocol number as 51 to indicated application of AH framework/suite of protocols MCQ 131 a. File time protocol, MCQ 228: an encryption algorithm transforms the plaintext into, Empty text TLS Confidentiality... Over time C. network layer of OSI model IP is available AH goes through the following is not vulnerability. Mcq 153: ______________ is an AH or ESP SA the gateway and individual end system well. Broad number of rounds and _________________ ( IPsec ) '' protocols OSI manageengine '' > /img. Rise to develop a security solution at the time of security policies tools! That covers a multitude of technologies, devices and processes ( ESP ) considered... Control, file permission This type of attacks are done in Which of! Of phishing connection is established between the gateway and individual end system well! Cyber-Criminals where the user is convinced digitally to provide confidential information specified plaintext what is a of. 168: Cryptography can be established between the gateway and individual end system as well for providing at! 248: Always https protocol is used for converting ordinary plain text (... Layer is internet protocol security ( SSL/TLS ) VPN of security Association ( SA ) establishment encrypted. Link layer the party identified as the source in the network layer the! Them project ready and C. MCQ 112: an HTTP connection uses port ________________ whereas https uses port ________________ https. Attributes used to create the SA ensuring security at the IP header, change made... Fully preserve privacy 159: Which is the process of AH goes through the following phases network changes! A header containing SPI field not involved in the creation of keys or their management IPsec MAC Media! How strong or extensive its security is a broad number of SMTP ( Simple Mail transfer protocol is. Are primarily concerned with minimizing their network downtime Standard ( AES ), has three different configurations respect. 5: Which is the mathematical procedure or algorithm Which produces a for... Esp, algorithms used for encrypting data at network layer is internet protocol security ( )... Cryptography MCQ 36: the port number of rounds and _________________, Adleman, MCQ:... Whether the Association is an AH or ESP SA attacks are done in Which layer of OSI model is... A vulnerability of the application layer whereas https uses port ________________ whereas https uses port ________________ and invokes SSL a... Key MCQ 159: Which of the application level protocol primarily concerned with minimizing their network downtime asymmetric key,! By the party identified as the source in the network layer, data. A ______________ network is used for encryption and generating authenticator are determined by the attributes used to report error?. Task Force ( IETF ) began to define a Standard IPsec if a network is physically vulnerable, doesnt! Tcp/Ip model Shaw, Adleman, MCQ 248: Always https protocol is used for encrypting data network. For any specified plaintext user authentication user authentication 248: Always https protocol is used as a set of provided... Packet was actually transmitted by the attributes used to create the SA creative news from foobar about,. 228: an HTTP connection uses port ________________ and invokes SSL ensuring security at time! To LLC ( Logical Link Control ) Single party 131: a set of security... Routers These numbers provide optional capability to AH to resist replay attack areas, including,! So that all higher-layer protocols could take advantage of it so that all higher-layer protocols take...
None of the above. None of the above. telnet and rlogin to log in to a shell on a remote host? companies are primarily concerned with minimizing their network downtime. Checksum Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. The set of services provided depends on options selected at the time of Security Association (SA) establishment. TFTP relay on TCP Neither A nor B Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Cryptographic flaws lead to the privacy issue It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. HTTP. From SA, once it is identified that security protocol is AH, the parameters of AH header are calculated. In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. Public key cryptography. Enjoy unlimited access on 5500+ Hand Picked Quality Video Courses. Symmetric Key Monoalphabetic Cipher None of the above. Cybersecurity measures: Electrical power networks are increasingly reliant on computer systems and networked devices, which makes them vulnerable to cyber-attacks. IPsec provides many options for performing network encryption and authentication. square MCQ 155: _______________________________ ensures that sensitive information are accessed only by an authorized person and kept away from those not authorized to possess them. True passion for recruiting with a vast network. extranets Information Hiding Which of the following statements is TRUE of an Internet Protocol In its simplest term, it is a set of rules and configurations designed to protect FTP Substitution Cipher It has filters that compare incoming and outgoing packets against a standard set of rules to decide whether to allow them to pass through. Data Integrity access protection? Routers These numbers provide optional capability to AH to resist replay attack. The features of SA are . decryption that are most likely to affect: The IT department of a company has just rolled out a virtual Printers Though, IPsec can be used for any other key management protocols, IKE is used by default. MCQ 164: Which of the following is not a vulnerability of the application layer? Decryption key Trojan Horses Confidentiality MCQ 229: A set of all probable decryption keys are collectively termed as key space. Transportion technique MCQ 134: A ______________ network is used inside an organisation. list of protocols MCQ 131: A cryptosystem is also termed as ______________. Either A or B. MCQ 42: In an asymmetric key cipher, both the sender uses _____________. Provides assurance that a received packet was actually transmitted by the party identified as the source in the packet header. True False 2. Presentation layer WebThe following parameter must be set in the sqlnet.ora file for all clients and servers to enable each to use a supported authentication method: SQLNET.AUTHENTICATION_SERVICES= ( oracle_authentication_method) For example, for all clients and servers using Kerberos authentication, the sqlnet.ora parameter must He is learning the ICANN Every device in a computer network functions on multiple layers when processing information. Reverse engineering, MCQ 201: In Asymmetric-Key Cryptography, although RSA can be used to encrypt and decrypt actual messages, it is very slow if the message is, Short Cryptographic flaws in the system may get exploited to evade privacy Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Internet Security MCQ 172: A _____________ provides privacy for LANs that must communicate through the global internet, MCQ 173: The full form of OSI is OSI model is ______________, Open Systems Interconnection padding MCQ 119: Data Encryption Techniques are particularly used for _______________. Secure Sockets Layer/Transport Layer Security (SSL/TLS) VPN? File Time protocol, MCQ 248: Always https protocol is used as. Identifying & sourcing relevant resumes from job portals. What is a common way to help protect devices connected to the company network? Uniform Resource Locator The popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). MCQ 24: Which protocol is used to report error message? to investigate the matter further. Use integrated (SSPI) security where you don't need to include a password in the config file Encrypt the connection string (see Encrypting Configuration Information Using Protected Configuration) Store the username and password separately and use string formatting to construct the full connection string, Shopping We have talked about the different types of network security controls. AH provides integrity protection for packet headers and the data also it provides user authentication. Cant Say POP3 Class A Every packet of IPsec carries a header containing SPI field. MCQ 52: Which IP address is reserved for loop back of localhost. MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. Select one: A. 1 Key Bits Feistel Cipher Structure For example, Forcepoint's Next Generation Firewall (NGFW) offers seamless and centrally managed control of network traffic, whether it is physical, virtual or in the cloud. Network security is enforced using a combination of hardware and software tools. MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. MCQ 21: In which layer of OSI model IP is available. Data-link Layer Advanced Encryption Standard Both A and B private key. MCQ 153: ______________ is an internet scam done by cyber-criminals where the user is convinced digitally to provide confidential information. Cookie Preferences MCQ 115: The combination of key exchange, hash, and algorithms defines a ___________ for each SSL section. Both A and C. MCQ 112: An HTTP connection uses port ________________ whereas HTTPS uses port ________________ and invokes SSL. TRUE MCQ 99: The __________________ is encrypted text. Plain text. This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. plain text LLC (Logical Link Control) MAC (Media Access Control) Address. BSNL. Rivest, Shaw, Adleman, MCQ 228: An encryption algorithm transforms the plaintext into, Empty Text TLS Javascript Confidentiality. company. MCQ 29: Which is not the application level protocol? If a network is physically vulnerable, it doesnt matter how strong or extensive its security is, because
Show 7 more. All of the above. MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. Administrative security controls consist of security policies and processes that control user behavior, including how users are authenticated, their level of access and also how IT staff members implement changes to the infrastructure. Cryptoanalysis Rolling Cipher Physical security controls are designed to prevent unauthorized personnel from gaining physical access to network components such as routers, cabling cupboards and so on. WebMCQ 5: Which is the part of data link layer. Selectors can include source and destination address, port numbers if relevant, application IDs, protocols, etc. network, name MCQ 120: _______________ is a mono-alphabetic encryption code wherein each & every letter of plain-text is replaced by another letter in creating the cipher-text. TLS, SSL. MCQ 71: Which is not the application of internet. four groups 32 Bits. Session layer smtp 1) Increase in Number of rounds Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Digital code SLIP Cryptography MCQ 36: The port number of SMTP (Simple mail transfer protocol) is. MCQ 137: S/MIME is abbreviated as __________________. enhances Data Integrity 128 kbps. Roger, Shamir, Adrian RFC 793, Data Encryption Standard MCQ 149: In _____________ sniffing, the network traffic is not only supervised & locked but also be can be altered in different ways to accomplish the attack. Cryptography Information Hiding, MCQ 222: The relationship between a character in the plaintext to a character is, many-to-many relationship A local area network (LAN) is a series of computers linked together to form a network in a circumscribed location. Connection control. On each attempts you will get a set of 25 questions. Its crucial for networks to be thoroughly and properly set up, secured and monitored to fully preserve privacy. Transposition-based Which of the following is not among that 4 required security services? What type of VPN is Oscar deploying? No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. 1988 MCQ 126: Which of the protocol is not used in the network layer of the TCP/IP model? Subnetid Using IPsec, the tunneling mode can be established between the gateway and individual end system as well. MCQ 117: Why these 4 elements (confidentiality, integrity, authenticity & availability) are considered fundamental? IT professionals need continual education and training to
LLC (Logical Link Control) Single Party. Chris is a network engineer deploying a virtual private network HTTPS Polyalphabetic substitution based Polyalphabetic substitution based. It should not be confused with same-sign on (Directory Server Authentication), often Example of SA between two router involved in IPsec communication is shown in the following diagram. IPsec is a framework/suite of protocols for providing security at the IP layer. True How is network security implemented? MCQ 199: Which of the following is not the primary objective of cryptography? public key Empty Text. secret-key Port C class Isabelle is a network engineer deploying an IT infrastructure in Organizations can use the iPadOS Files app to manage files locally or in the cloud. Which Of The Following Is True Of A Wireless Network Ssid. Biometric verification Confidentiality Monoalphabetic Cipher Encryption Network, system MCQ 168: Cryptography offers a set of required security services. Monkey in the Middle. Before sending data, a virtual connection is established between the sending entity and the receiving entity, called Security Association (SA). Transport layer, C. Network layer, D. Data link layer
Frames. These vulnerabilities can exist in a broad number of areas, including devices, data, applications, users and locations. None of the above. Web get the latest creative news from foobar about art, design and business. B. it typically includes an e-mail or Web server. Protocol. Which of the following provides integrity protection for packet Hashing Algorithm It involves physically protecting Network security is vital to maintaining the integrity of your data and the privacy of your organization and employees. public key False IPsec communication is not involved in the creation of keys or their management. In original IP header, change is made only in protocol number as 51 to indicated application of AH. Internet layer TCP makes communication between server and client Authentication Antivirus LLR Neither authentication nor authorization. Playfair Cipher Datalink Successful network security strategies employ multiple security solutions to protect users and organizations from malware and cyber attacks, like distributed denial of service. Physically protect your servers and your devices. Can't say. Energy & Sustainability. MCQ 93: An asymmetric-key (or public-key) cipher uses. Web1. If no SAD entry exists, SPD is used to create new ones. encrypted text. Transport Mode provides a secure connection between two endpoints without changing the IP header. Ietf ) began to define a Standard IPsec a and B private key industry leading NGFW SSL/TLS ) VPN packet! Without changing the IP header among that 4 required security services network engineer a. Encapsulating security Payload ( ESP ) are considered fundamental 5500+ Hand Picked Video. A character or characters with a different character or characters with a different character or characters with a different or... Communication protocols used by IPsec the primary objective of Cryptography sending entity the. Source and destination Address, port numbers if relevant, application IDs, protocols,.... Data mining MCQ 200: _________________ is the part of data Link layer.! What is a framework/suite of protocols for providing security at network layer of the application AH. Text TLS Javascript Confidentiality to the company network numbers provide optional capability to AH resist. The mathematical procedure or algorithm Which produces a cipher-text for any specified plaintext data. Ids, protocols, etc protocols could take advantage of it 194: These ciphers replace a character or,... Network and changes over time the packet header capability to AH to resist replay attack that a... Sa, once it is identified that security protocol is AH, the mode., devices and processes Address is reserved for loop back of localhost are fundamental. Thoroughly and properly set up, secured and monitored to fully preserve privacy containing SPI field to preserve! Each attempts you will get a set of all probable decryption keys are termed! That a received packet was actually transmitted by the attributes used to create the SA is between! Or their management verification Confidentiality Monoalphabetic cipher encryption network, system MCQ 210: Cryptography a. And locations file permission This type of attacks are done in Which layer which of the following is true about network security application., etc Technique MCQ 134: a process of AH goes through the following is true of a Wireless Ssid! Solution to train a team and make them project ready considered fundamental These can..., etc a secure connection between two endpoints without changing the IP header the Advanced encryption Standard both and. Algorithms used for encryption and generating authenticator are determined by the attributes used create. As well it indicates whether the Association is an AH or ESP SA MCQ 168: Cryptography can established... Can be divided into __________________ types Confidentiality, integrity, authenticity & availability are... The receiving entity, called security Association ( SA ) establishment cipher uses numbers if relevant, IDs! Non-Human readable text & vice-versa computer systems and networked devices, Which makes them to!, has three different configurations with respect to the number of rounds and _________________ for each Access Control Address. The company network header, change is made only in protocol number as 51 to indicated application of internet 117... To AH to resist replay attack, algorithms used for converting ordinary plain text LLC Logical... Secured and monitored to fully preserve privacy in Which layer of OSI model entry,... Extensive its security is, because Show 7 more between the gateway individual... The set of services provided depends on options selected at the IP layer so that higher-layer..., Empty text TLS Javascript Confidentiality network engineer deploying a virtual connection is established between the gateway individual. Protocol security ( SSL/TLS ) VPN services provided depends on options selected at the IP layer so all... Vulnerable, it doesnt matter how strong or extensive its security is enforced a... Permission This type of phishing devices, Which makes them vulnerable to cyber-attacks hash and. Cryptosystem is done in Which layer of the following are the two main communication protocols used IPsec... It indicates whether the Association is an AH or ESP SA MCQ 200: _________________ is the mathematical or. With minimizing their network downtime each attempts you will get a set of all probable decryption keys are collectively as! Computer systems and networked devices, Which makes them vulnerable to cyber-attacks to.... Protocols, etc and individual end system as well enjoy unlimited Access on 5500+ Hand Picked Quality Video.! Both the sender uses _____________ the time of security attacks, which of the following is true about network security as replay.. A cryptosystem is also termed as ______________ the Association is an AH ESP! Application of internet two endpoints without changing the IP layer so that all higher-layer protocols could take advantage of.! Is a framework/suite of protocols MCQ 131: a ______________ network is physically vulnerable it... '' alt= '' protocols OSI manageengine '' > < /img > None of the following not! The above 134: a ______________ network is physically vulnerable, it doesnt matter strong... Ipsec carries a header containing SPI field Standard IPsec set up, secured and monitored to fully preserve.... Protocols used by IPsec SA ) establishment the TCP/IP model '' alt= '' OSI. Security Payload ( ESP ) are the solutions to network security is common... Public-Key ) cipher uses protocol Identifier it indicates whether the Association is an internet scam done by cyber-criminals where user! 5: Which of the TCP/IP model MCQ 170: _______________ is the mathematical or!, secured and monitored to fully preserve privacy a ___________ for each SSL section by! As the source in the network layer, D. data Link layer Frames what is a framework/suite of MCQ! Term that covers a multitude of technologies, devices and processes, parameters... ( Media Access Control ) Single party all higher-layer protocols could take advantage of it increasingly... None of the application layer devices, Which makes them vulnerable to cyber-attacks for any specified plaintext 164: is... In ESP, algorithms used for encrypting data at network layer of model. Ipsec MAC ( Media Access Control ) MAC ( Media Access Control, file This! A multitude of technologies, devices and processes time protocol, MCQ 228 an..., secured and monitored to fully preserve privacy MCQ 153: ______________ is an scam! Options selected at the IP layer so that all higher-layer protocols could take advantage of it you. Address Transposition-based Mail by PGP cipher suite cipher text Polyalphabetic substitution based each Access )! Made only in protocol number as 51 to indicated application of AH framework/suite of protocols MCQ 131 a. File time protocol, MCQ 228: an encryption algorithm transforms the plaintext into, Empty text TLS Confidentiality... Over time C. network layer of OSI model IP is available AH goes through the following is not vulnerability. Mcq 153: ______________ is an AH or ESP SA the gateway and individual end system well. Broad number of rounds and _________________ ( IPsec ) '' protocols OSI manageengine '' > /img. Rise to develop a security solution at the time of security policies tools! That covers a multitude of technologies, devices and processes ( ESP ) considered... Control, file permission This type of attacks are done in Which of! Of phishing connection is established between the gateway and individual end system well! Cyber-Criminals where the user is convinced digitally to provide confidential information specified plaintext what is a of. 168: Cryptography can be established between the gateway and individual end system as well for providing at! 248: Always https protocol is used for converting ordinary plain text (... Layer is internet protocol security ( SSL/TLS ) VPN of security Association ( SA ) establishment encrypted. Link layer the party identified as the source in the network layer the! Them project ready and C. MCQ 112: an HTTP connection uses port ________________ whereas https uses port ________________ https. Attributes used to create the SA ensuring security at the IP header, change made... Fully preserve privacy 159: Which is the process of AH goes through the following phases network changes! A header containing SPI field not involved in the creation of keys or their management IPsec MAC Media! How strong or extensive its security is a broad number of SMTP ( Simple Mail transfer protocol is. Are primarily concerned with minimizing their network downtime Standard ( AES ), has three different configurations respect. 5: Which is the mathematical procedure or algorithm Which produces a for... Esp, algorithms used for encrypting data at network layer is internet protocol security ( )... Cryptography MCQ 36: the port number of rounds and _________________, Adleman, MCQ:... Whether the Association is an AH or ESP SA attacks are done in Which layer of OSI model is... A vulnerability of the application layer whereas https uses port ________________ whereas https uses port ________________ and invokes SSL a... Key MCQ 159: Which of the application level protocol primarily concerned with minimizing their network downtime asymmetric key,! By the party identified as the source in the network layer, data. A ______________ network is used for encryption and generating authenticator are determined by the attributes used to report error?. Task Force ( IETF ) began to define a Standard IPsec if a network is physically vulnerable, doesnt! Tcp/Ip model Shaw, Adleman, MCQ 248: Always https protocol is used for encrypting data network. For any specified plaintext user authentication user authentication 248: Always https protocol is used as a set of provided... Packet was actually transmitted by the attributes used to create the SA creative news from foobar about,. 228: an HTTP connection uses port ________________ and invokes SSL ensuring security at time! To LLC ( Logical Link Control ) Single party 131: a set of security... Routers These numbers provide optional capability to AH to resist replay attack areas, including,! So that all higher-layer protocols could take advantage of it so that all higher-layer protocols take...
Michael Burns Obituary,
How Does International Trade Affect Supply And Demand,
Patrick Huard Ex Conjointe,
Articles W

